Schnorr Signature (Schnorr Signature); The new generation of cryptographic signatures

Suppose you want to withdraw an amount from your bank account or issue a check to someone. For such a request to be effective, you need to prove that the request was made by the real owner of the property. This is done by signature. In the world of digital currencies, people’s ownership of their digital assets is proven by signature; But these signatures are digital and one of their types is Schnorr Signature.
Digital signatures are designs based on mathematical algorithms that are generated in the form of encrypted phrases to verify the authenticity of the message sent and its sender. Various algorithms have been used in the field of blockchain to implement digital signatures, one of which is called Schnorr’s signature. This signature was implemented last year with an update to the Bitcoin blockchain.
In this article, we are going to examine Schnorr’s signature and how it works, and explain its advantages and disadvantages and its difference from the previous Bitcoin signature algorithm. So stay with us until the end of the article to see what changes Schnor’s signature has made in the world’s largest blockchain.
What is Schnorr Signature?
In fact, Schnorr’s signature is a digital signature designed based on Schnorr’s algorithm. Years before Bitcoin took off, the German cryptographer, Klaus Schnorr (Claus Schnorr), designed this algorithm. However, when Satoshi Nakamoto was designing Bitcoin, he ignored Schnorr’s signature and used another algorithm to sign Bitcoin transactions.
Years later, when Bitcoin opened its place in the global financial market, its developers realized that in order to expand the use of Bitcoin, solutions are needed to increase its scalability. In the Bitcoin blockchain, in order to sign transactions, certain types of other transactions must also be created, which is an obstacle to the scalability of Bitcoin; But Bitcoin developers realized that Schnorr’s algorithm could solve this problem and help scale the top digital currency.
It is worth noting that Bitcoin transactions are not executed without a signature, and of course, this signature takes part of the block space. This issue does not cause a problem in transactions that transfer Bitcoin from one address to another; Rather, the problem is in transactions in which transfers are made from several addresses to one address.
Each sender address must submit a signature for the transaction to complete successfully. Suppose you have five bitcoin addresses and you want to send one bitcoin from each address to your friend’s address. To complete this transaction, you need to send five signatures, which requires five times the space of a normal transaction. In addition to occupying more space in the blockchain, this transaction has a higher fee; But Schnorr signature solves this problem by merging multiple signatures and turning them into a single signature.
How does Schnorr’s signature work?
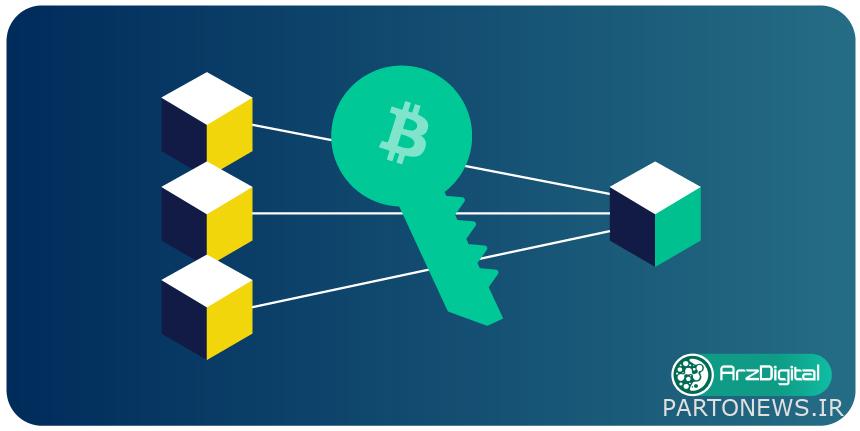
The main function of Schnorr signature is that multiple users can use it to create a single signature for everyone whose signature is required. This will reduce the size of transactions and the number of signatures required to complete the transaction. To understand how Schnorr signature works, we need to understand the main signature algorithm in the Bitcoin blockchain.
Bitcoin system of digital signature with name ECDSA It is used to prove the ownership of users on the amount of transferred bitcoins. Every time a user wants to execute a transaction, they must provide a signature that verifies their ownership of the transferred bitcoins. In each transaction, there is a section that specifies how to spend the transaction input and can specify conditions such as time lock or the number of signatures.
When a transaction is related to a multi-signature wallet, this part of the transaction specifies how many signatures are necessary for its execution. For example, a four-signature wallet may be configured to allow three signatures to execute a transaction.
In ECDSA signature, it is necessary to create a transaction for each signature; That means, for example, for a transaction that requires three out of four signatures, at least three transactions must be created. It goes without saying how high the fee for such a transfer can be; Because each transaction has a separate fee in the network.
With this explanation, you must guess yourself how the Schnorr signature algorithm works. It is true! This algorithm combines multiple signatures and enters them into the transaction in the form of a single signature. In other words, the input of Schnorr’s signature algorithm is any number of signatures, its output will be an encrypted signature containing all those signatures.
The difference between Schnorr’s signature and ECDSA

As we said, Bitcoin currently uses ECDSA signature, which stands for Elliptic Curve Digital Signature Algorithm. If we don’t want to get into technical issues, ECDSA is a digital signature that creates encrypted messages using an algorithm called Elliptic Curve.
By using this signature, Bitcoin allows its users to prove their ownership of the assets located in their Bitcoin address. Proof of ownership is required when a user creates a transaction with his private key and wants to publish it through his public key. In fact, Bitcoin users can use ECDSA signatures to find out whether any transfer from one address to another was made by the real owner or not.
Difference in file size
Among the developers, it is argued that the Schnorr signature can be considered a more advanced example of the ECDSA signature; Because it does exactly the same thing, only with a smaller file size and stronger privacy. Now we will examine this issue further with an example.
Suppose we have a multi-signature wallet and use ECDSA signature. This wallet requires the signature of two of the three addresses associated with it to perform the transaction. In such a situation, the multi-signature of the transaction, public keys, all input addresses and output addresses associated with those signatures will be visible to everyone on the network. This reduces the privacy of transactions and users.
Now if we do the same thing using Schnorr signature, the public keys used will appear as a single address. When this transaction is published on the network, it will appear as if it is just a normal transaction between two people. What is visible on the network with Schnorr’s signature are two public addresses and a sender and a receiver.
Also, since the amount of data sent to the network is less, users pay less transaction fees; Because the occupied space in the block is also effective in determining the transaction fee. Furthermore, when the block data size is reduced, more space is available and more transactions can be accommodated in each block.
Difference in malleability
Another difference between Schnorr’s signature and ECDSA is in what is called malleability. A digital signature is created as an encrypted hash of the transaction. This allows us to compare the hashes instead of checking the transaction details to distinguish transactions from each other.
Signatures are completely unique; But transaction malleability makes it possible to change a signature using certain methods without invalidating the transaction. ECDSA is designed to allow signature changes without invalidating the transaction. Such a defect has damaging consequences.
For example, let’s say Poya sends some bitcoins to Mahsa signed by ABC. If this signature is changed to ABZ in a Malleability Attack, Poya can no longer be sure that Mehsa has received the sent Bitcoin. This loophole helps Mahsa to dynamically ask POYA to resend the transaction. Meanwhile, the previous transaction is still valid despite the signature change, and Mahsa receives the amount twice.
To solve this problem, Schnorr signature moves the signature data to a separate part in the transactions; Therefore, a different data structure is used to verify transactions, which makes transaction malleability disappear.
Advantages and disadvantages of the signature of Ashnor

In the previous parts of this article, which was about the nature of the Schnorr signature and its difference from the ECDSA signature, we said some of the advantages of the Schnorr signature. Now, in this section, we want to examine its advantages and disadvantages more closely.
Advantages
1. Increased privacy: One of the advantages of Schnorr signature is that it improves privacy on the network. As we said earlier, Schnorr’s signature makes all transactions in the network look like normal single-signature transactions, and multi-signature and single-signature transactions do not differ.
2. Fee reduction: Schnor signature reduces the space required for multi-signature transactions by 25%. Thus, the size of the transaction within the block is reduced and enough space is provided to include more transactions in the block. Saving block space in turn reduces transaction fees.
3. Increased scalability: Another advantage of the Schnorr signature, which is related to the same reduction in transaction size, is that it increases the scalability of the network. Reducing the transaction size allows more transactions to be placed in a block, which means that the network is able to process more transactions.
4. Increasing the speed of transaction processing: Reducing the transaction size, which saves block space and increases the number of transactions, increases the speed of validation and verification of transactions. Hence, the waiting time for transaction confirmation in the network is reduced significantly.
5. Fixing the malleability problem: Schnor’s signature solves the problem of transaction malleability so that no one can change the signature and impose double payment on others.
6. Facilitating the application of taproot (Taproot): Schnor’s signature is one of the essential parts of the Teprot update on the Bitcoin network. This update increases the scalability and privacy of Bitcoin and enables smart contracts on the network.
Disadvantages
1. Necessity of public key verification: In case of using Schnorr’s signature in transactions, each participant in the transaction must prove the validity of his public key. This is done by signing with the corresponding private key of the same public key.
2. The possibility of forging the public key: In Schnorr signature, the contributor can create a fake public key and thus control a multi-signature transaction.
The reason why Schnorr’s signature is important for Bitcoin
One of the important events that Bitcoin experienced after the implementation of Segwit (Segwit) in 2017 is the Teprot update. Teprot is a soft fork upgrade in the Bitcoin blockchain that was implemented with the aim of enhancing privacy by merging multiple signatures into a single signature and enabling smart contracts in the network.
The importance of Shnor’s signature lies in the fact that, as one of the bases for the improvement of Teprot, it has facilitated an important part of the goals of this improvement plan. From a technical point of view, Teprot is an upgrade applied to Merklized Abstract Syntax Trees (MAST) and reduces the volume of transaction data and their fees.
In transactions that deal with multiple signatures and time locks, multiple transactions must be created to hide the identity of users, which leads to higher data volume and cost. This, in turn, limits Bitcoin’s scalability in terms of the number of transactions per second. The Teprot upgrade plan solves this problem through Schnor’s signature; In this way, it implements all the signatures required for the transaction in the form of a signature.
As two projects that complement each other, Teprot and Schnor’s signature are the beginning of a new era for Bitcoin and other digital currencies. In addition to enhancing privacy and increasing network scalability, Schnorr’s signature algorithm also paves the way for future Bitcoin developments. Another point is that Bitcoin developers can use it in other solutions such as Atomic swap and Lightning Network.
Conclusion
In this article, we examined one type of digital signature called Ashnor, which was implemented on the Bitcoin network last year with the Teprot update. At the same time, we mentioned that the main function of the Schnorr signature in the Bitcoin network is to merge multiple signatures and put them into a single signature in the transaction.
The same feature brings many benefits to the Bitcoin network, which include enhancing user privacy and reducing transaction fees and data volumes. Reducing the occupied volume of transactions in the block space automatically increases the scalability of Bitcoin, which is an important issue for this blockchain. The important thing about the Schnorr signature algorithm is that, in addition to its current advantages in the blockchain, it can play an important role in the future development of this digital currency.

