Sleep Minting (Sleep Minting); A potential risk lurking for NFT buyers

Fraud methods in the world of digital currencies are very diverse, and along with the development of this space, its number also increases. Some of these threats specifically target digital currency buyers and holders, while others attempt to exploit nascent concepts such as virtual tokens (NFTs). Sleep Minting is one of the new fraud methods in the blockchain and digital currency space, which finds its victims in the field of non-homologous tokens.
Such scams can cause various problems in the NFT market by making users distrustful; For this reason, gaining more knowledge and better familiarity with how to review smart contracts and consider possible problems can be of great help to those interested in non-traditional tokens.
In this article, we are going to introduce sleep minting and how it happens and some important examples of this fraud. Also, by telling you how to identify this scam and how to deal with it, we will help you to avoid falling into the trap of these scams by raising awareness.
Sleep minting in simple language
Sleep minting is a type of fraud in the space of non-traditional tokens that is done by counterfeiting the token. In this method, the fraudster creates a fake non-genuine token through the wallet of a well-known creator and at the same time provides a way to retrieve and return the fake token to his wallet. This method of fraud exploits the bugs and vulnerabilities of smart contracts, especially in the non-proprietary token space, and clearly affects the most important feature of NFT tokens, i.e. their authenticity.
In 2021, at least $27 billion of digital currency was transferred to Ethereum-based asynchronous token smart contracts, namely ERC721 and ERC1155. The movement of this huge capital along with the emergence of popular projects such as “Board IP Yacht Club” (BAYC) and “CryptoPunks” and “Doodles” show the attractiveness of this field of digital currencies for people all over the world.
However, we must not forget that the craze of non-coin tokens can be a big trap for users, especially newcomers. What makes it easier to commit such scams is actually the complexity of the NFT smart contract code; A feature that does not allow these types of hacks to be easily traced.
How does sleep minting work?Thegive
The fraudster in Sleep Minting first creates a token through the wallet address of a famous NFT creator and then transfers it to his own wallet; While pretending that the manufacturer has done this transaction. In this method, the hacker implements a customized asymmetric token contract similar to other common contracts in this space; But it doesn’t do its security check purposely. Thus, the hacker creates the false impression that he has legitimately received a valuable asynchronous token from a legitimate creator.
This is while the main artist whose name the token was created is not aware of this happening. In fact, in this method, the fraudster combines the malicious code with the original code of the token contract so that he can send the fake token to his wallet without the need to get permission from the creator’s wallet. Thus, the hacker sends the fake token to his own wallet without the need to get permission from the creator’s wallet, and then sells it in the form of a valid token on a secondary market such as OpenSea or LooksRare.
An example of sleep minting
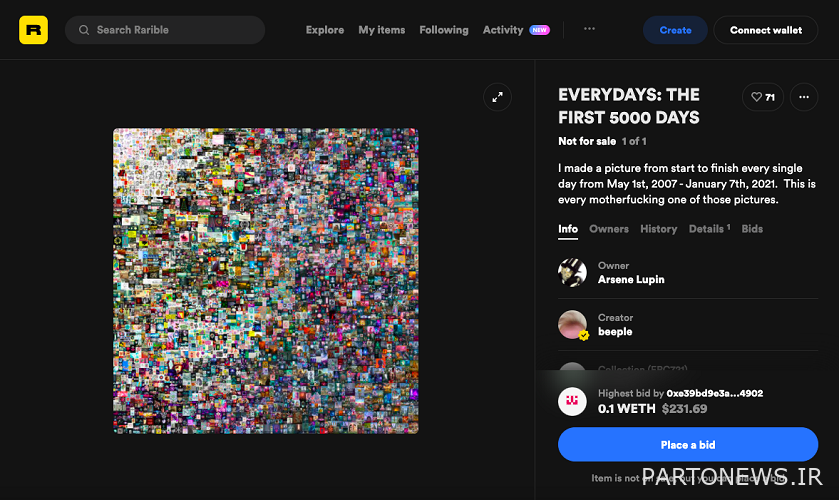
To better understand how this scam works, let’s take a look at the first example. On April 4, 2021, an anonymous hacker with the nickname Monsieur Personne, which means “Mr. Nobody” in French, managed to perform the first NFT slip minting. In this scam, the hacker created a “second version” of the artwork “Everydays: The First 5,000 Days” by Bippel. It should be noted that the value of the original version of this work is 69.3 million dollars.
Read more: Know the most expensive NFTs in the world
In this action, the hacker did not right-click on the JPEG image of the work to save it under his name. Instead, he created a second, fake version of the work by exploiting PayPal’s wallet and then transferring it to his own wallet. In fact, the fraudster does two malicious transactions for this: 1. Creates a fake token; 2. Transfers it to your account. These transactions can only be done if a valid signature is created between the two parties.
Monsieur Persson’s fake contract was written in such a way that it did not need this security check, i.e. the signature of the parties on the blockchain. Thus, the hacker took possession of the token to sell it on the secondary market or send it to another wallet and pocket the profit from its sale.
Why is sleep minting dangerous for the market?
The main value of non-traditional tokens is the uniqueness of their creator. Sleep minting can undermine the credibility of these non-monogamous tokens. If these unique tokens can be easily forged and sold, there will be no purpose or value left for them. In fact, sleep minting is considered a threat to the authenticity of the NFT token market and can significantly reduce the attraction of capital and investors to this market.
In addition, the biggest targets of sleepminting fraudsters are prominent creators of these tokens who have a large following on social media. Thus, fraudsters are more likely to sell their fake token before being detected and make a profit by tricking people.
Also, this vulnerability in ERC721 and ERC1155 contracts related to non-equivalent tokens could pave the way for further larger scams or open the way for ERC20 tokens to be found vulnerable. The good news is that there are still ways to identify these tokens, and only newcomers and uninformed people may be affected.
How to identify sleep minting scams?
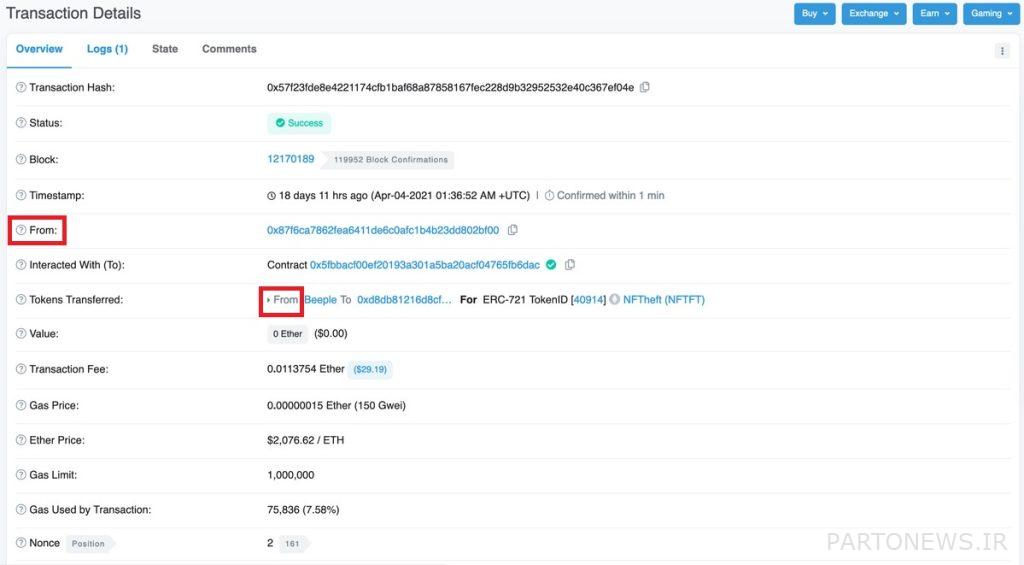
The most important measure to identify fake Sleep Minting tokens is the proper use of the Etherscan browser or other blockchain browsers. Using these browsers, you can check the token’s previous transaction history and make sure the seller is a seasoned user.
Tokenview section (Token View) helps users to check the details of tokens more carefully. Since the hacker cannot have the creator’s private key and sign on his behalf, the mint transaction cannot be initiated. For example, in the example of the Beeple effect transaction, you can match the sender address of the token creation transaction with the original Beeple address. If it doesn’t match, you’re probably dealing with a fraudulent transaction.
Additionally, services such as fraud detection bots specific to sleep minting instances on Forta’s decentralized monitoring platform will provide you with alerts on fraud cases. Also, if you suspect that the token might be fake, you can contact the original creator and ask them to take back control of the token. Do not underestimate your sixth sense. If you have an offer to buy a token that seems too tempting, it is better to be skeptical.
Finally, if you have doubts about your token, you can immediately sell the token with a percentage discount on other token trading platforms; Of course, note that it is not always easy to find a suitable buyer for these tokens, and you may suffer a loss. In general, being aware of possible risks at the time of purchase and paying attention to the details of the token will help you enter the investment market with more ease.
How to avoid the danger of sleep minting?
In addition to what we have said, there are also some simple tips that will help you avoid falling into sleep minting scams as much as possible. In the following, we mention some of these solutions:
- Before buying or receiving a foreign token, be sure to check the creator and origin of the token.
- If you are not familiar with NFT addresses and smart contracts, be sure to read up on this before purchasing.
- As much as possible, try to increase your awareness and knowledge about non-coin tokens and how to create them.
- If you receive a token from an unknown source, remove it from your wallet immediately.
- If you suspect that you are a victim of sleep minting, contact the original token creators and ask them for help if possible.
- Report suspicious activity to law enforcement and notify other users through social media and forums.
In addition, creators of non-monogamous tokens should also exercise caution in this regard. For example, they can refuse to allow users of this suspected scam to create NFT tokens in their wallets and monitor any suspicious activity related to their wallets. It is worth noting that reputable creators of non-monogamous tokens are also victims of sleep minting and may lose their credibility and the value of their works.
TotalTheclassification
In this article, we got acquainted with one of the new types of frauds in the space of digital currencies called sleep minting. In the sleep minting method, the hacker creates a fake token by abusing the wallet of one of the authentic token creators; But he pockets the profit from the sale and transfer of the token. We also reviewed the steps involved in the first example of sleep minting and explained why this type of fraud can be costly and destructive to the entire cryptocurrency space. At the end, we mentioned the practical methods to identify and avoid the sleep minting scam.
With the expansion of the space of digital currencies, hackers are also turning to new methods and approaches for hacking and fraud. The development of new areas of fresh technologies such as blockchain and digital currencies, along with all their achievements, makes the weaknesses of these technologies available to fraudsters as an excuse to infiltrate the system. However, the good news is that these inevitable exploits can help cover weaknesses and create deterrent rules to prevent similar problems from happening again.
In fact, the move of an unknown hacker with the nickname Monsieur Persson with the aim of forging one of the most valuable tokens of the market made the users of this field realize the importance of reading smart contracts correctly and analyzing them more. Examples of sleep minting further highlighted the importance of expanding and increasing knowledge about the security of non-coin tokens. Also, this issue reminded me of one of the principles of blockchain, i.e. not needing to trust the transaction party. Simply put, if you know how to read a smart contract, you don’t need to trust the other party.

