Telegram responded to the attacks of the CEO of WhatsApp; you can’t prove your words!

In a statement, Telegram responded to the attacks of the CEO of WhatsApp. They say, the competitor’s talk is full of flaws and not technically proven.
Yesterday, Will Cathcart, the executive director of WhatsApp at Meta Company, attacked the rival messaging app, Telegram. Cathcart claimed that Telegram is not secure at all and transmits users’ messages without an end-to-end (E2EE) protocol. This executive director also stated that Telegram provides all the information that the Russian government needs from its users. Now Telegram has responded to the attacks of the CEO of WhatsApp.
Read more:
WhatsApp CEO’s strong attack on Telegram: You are invalid and a tool of Russian espionage
Answers of the Telegram spokesperson to the attacks of the CEO of WhatsApp
Telegram spokesperson Remi Wan says that Wired’s report has many flaws and that its author completely ignored Telegram’s responses and was completely biased. Telegram’s spokesperson has published a photo in which he has answered Wired magazine’s claims about location tracking of its users. He says this has only happened to 0.01% of people.
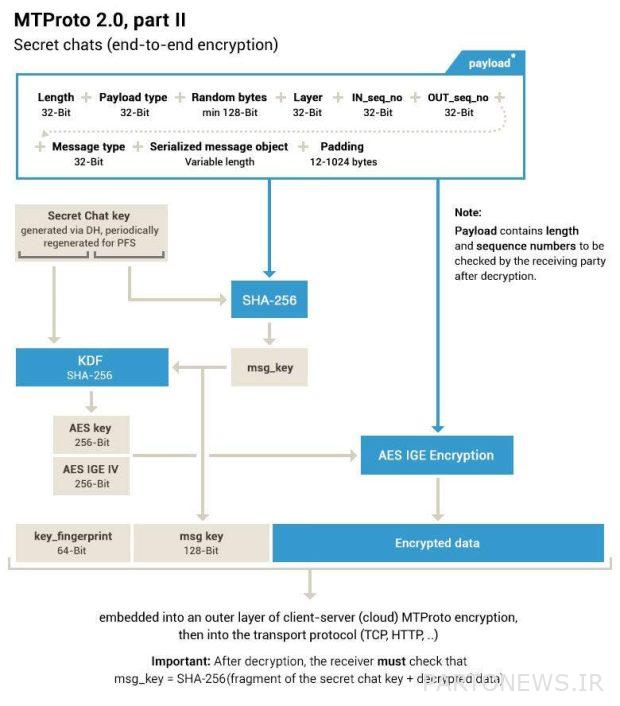
The release of Telegram’s security protocol process in response to WhatsApp attacks
Regarding the privacy of Telegram’s secret chat section, which was attacked by the WhatsApp CEO, Vaughan also says that Cathcart was wrong about Telegram’s end-to-end encryption protocol not being approved. A team from Italy’s University of Udine, who use Telegram to keep their chats secure, confirms the safety of the MTProto 2.0 protocol. Keep in mind that Telegram is an open source application and uses version 5.13 of Reproducible Builds.
Reproducible Builds means that you can compile publicly available source code and verify that the resulting device code is identical to code hosted on the Apple App Store, Google Play Store, and Telegram’s own website. But Telegram’s servers are not open source, although the Udine team confirms that the MTProto 2.0 protocol can also engage malicious servers.
The group points to a problem that could compromise the security of secure chats. When a secret chat is initiated, it is critical that the user’s fingerprint is verified through a secure external channel. Otherwise, attacks become possible. This means that a third-party channel can eavesdrop and even change messages. Researchers say that such a thing is also possible in the Signal application.
So if you’re using any of these apps, make sure you set up your fingerprint on the device properly, experts say. As long as you don’t do it correctly, the security chat secret will look like a regular chat.
What do you think about the attacks of the WhatsApp CEO on the Telegram messenger? Do you believe that they are also spying for Russia? Or do they want to reduce the popularity of the rival application by raising these rumors?

