Vulnerability in Lenovo laptops and unauthorized admin access

In a new vulnerability, it was found that Lenovo ThinkPad and Yoga series laptops in the ImControllerService service allow unauthorized access to the admin system and execute commands. CVE-2021-3922 and CVE-2021-3969 security vulnerabilities in ImControllerService are part of the Lenovo System Interface Foundation and are available in versions 1.1.20.3 and below.
System Interface Foundation Service is a service and application that is installed on almost all Lenovo laptops in the Windows operating system and provides Lenovo update, troubleshooting and configuration services for Lenovo Vantage. When you are browsing Windows service, this Lenovo service called System Interface Foundation Service is visible. The service is also used to run Lenovo apps such as Lenovo Companion, Lenovo Settings and Lenovo ID, and is installed by default on Yoga and ThinkPad series laptops.
This Lenovo interface also offers additional capabilities for system power management, system optimization, driver updates, and applications. If you disable this service in windows service, the applications and features mentioned above will be disabled. The vulnerabilities were discovered by security researchers at the NCC Group, who reported details of their investigation to Lenovo on October 29 this year. Lenovo released a security update for the vulnerability on November 17, and almost a month later on December 14 (December 23). General And advised customers and users to do the update.
Vulnerability in system components Lenovo laptops
Because ImController needs to connect to Lenovo servers to fetch, install, run child processes, and configure and maintain the system, it needs SYSTEM privileges. Administrator-level access to a system in Windows creates the highest user privilege, and the operating system allows the admin user to execute any command. In fact, if a simple, unauthorized user accesses SYSTEM privileges, he will be free to install any malware or backdoor and make any changes to the operating system.
This vulnerable Lenovo service requires a lot of child processes and parallel processing, which is why it opens several named pipe servers that ImController uses to communicate with the child process. When ImController needs one of these services to execute a command, it connects to the named pipe and issues the serialized XML command to execute. Unfortunately, this service does not securely communicate between the child process and admin access and fails to validate the XML serialized command. All of this means that any other process with these conditions can connect to the child process and execute its own commands, even those that contain malicious commands.
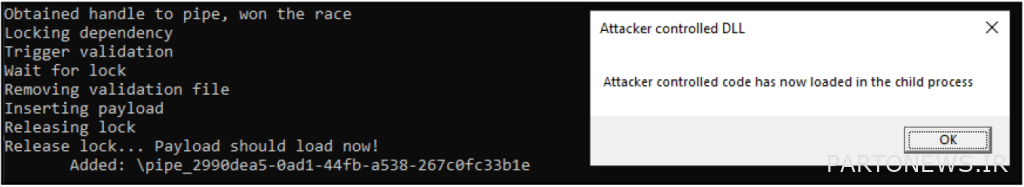
researchers NCC Group They stated that their proof of concept never encountered an obstacle to connecting the named pipe, which means that the exploitation they have created is very stable and feasible. The second security flaw is related to Time-of-check-to-time-of-use (TOCTOU), which enables the attacker to temporarily stop the loading process of a valid plugin in ImControllerService and replace it with a dll file of your choice. When the file is replaced and the process continues, the dll file is executed, leading to an attacker accessing the admin system.

Update, the only solution available
Lenovo advised all Windows users of their laptops with ImController version 1.1.20.2 or lower installed to upgrade to the latest version (1.1.20.3).
Follow the steps below to specify your executable version:
Go to the following path C: Windows Lenovo ImController PluginHost
on Lenovo.Modern.ImController.PluginHost.exe Right click and select Properties Choose
On the tab Details click
Finally you can see the file version.
Lenovo does not recommend removing the ImController or Lenovo System Interface Foundation from laptops, and acknowledges that doing so could adversely affect some of the device’s performance.
Score: 5.0 Out of 5 (1 vote)
wait a little…

